动态调试
Java层动调
在Manifest给 AndroidManifest.xml 设置:
android:debuggable="true"
使用apktool工具解包修改manifest,重打包回去之后进行签名;
先对文件进行对齐:
zipalign -p -f -v 4 input.apk output_unsigned.apk
加签名,其中 abc.keystore 是通过 androidstudio 生成的签名文件,也可以自行用工具生成,参考:APK反编译、重打包、签名之apktool实现_apktool反编译还是乱码-CSDN博客:
apksigner sign --ks abc.keystore output_unsigned.apk
安装到手机上,以调试模式启动:
adb shell am start -D -n com.chick.androdbgme/.MainActivity
用jeb attach上去,运行修改后代码。
Native层调试
参考:
IDA以Debug模式启动APK调试SO的JNI_OnLoad函数的两种办法
Frida
Frida是一款基于Python + JavaScript 的hook框架,本质是一种动态插桩技术。可以用于Android、Windows、iOS等各大平台,其执行脚本基于Python或者Node.js写成,而注入代码用JavaScript写成。
原理
frida使用的是动态二进制插桩技术(DBI)。
插桩技术是指将额外的代码注入程序中以收集运行时的信息,可分为两种:
源代码插桩 (Source Code Instrumentation, SCI):顾名思义,在程序源代码的基础上增加(注入)额外的代码,从而达到预期目的或者功能;
二进制插桩 (Binary Instrumentation):额外代码注入到二进制可执行文件中,通过修改汇编地址,改变程序运行内容,运行后再返回到原来程序运行出处,从而实现程序的额外功能。
静态二进制插桩 (Static Binary Instrumentation, SBI):在程序执行前插入额外的代码和数据,生成一个永久改变的可执行文件。
动态二进制插桩 (Dynamic Binary Instrumentation, DBI):在程序运行时实时地插入额外代码和数据,对可执行文件没有任何永久改变。
DBI能做什么?
- 访问进程的内存
- 在应用程序运行时覆盖一些功能
- 从导入的类中调用函数
- 在堆上查找对象实例并使用这些对象实例
- Hook,跟踪和拦截函数等等
安装
安装frida包
1 | pip install frida -i https://pypi.mirrors.ustc.edu.cn/simple/ |
配置代码提示
安装node.js后,新建文件夹,在目录下执行命令:
1 | npm i @types/frida-gum |
配置成功,可以在当前目录下编写js代码。
Server环境配置
Releases · frida/frida (github.com)
下载Frida的Server端->frida-server-15.1.4-android-arm64.xz,这里版本要与hook程序架构适配。
然后push到手机的data/local/tmp目录下,和IDA的动态调试有点类似。
1 | # 查看设备实际 CPU ABI,用于下载对应的frida-server-x.x.x-android-xxx.xz |
如果能显示进程列表说明环境搭建完成:
1 | # PC端输入 |
Frida Hook
执行Hook
启动时hook:
1 | # 将 xxxxxx 换成你手机里安装好的任意apk包名 |
启动apk后hook:
1 | frida -U -f com.test.apk |
Java层Hook
Frida的Java层重要函数
使用 java平台—>Java.perform(function () {} 获取 Java类 —>Java.use(className)。
当获取到Java类之后,直接通过 <wrapper>.<method>.implementations = function() {} 的方式来hook wrapper类的method方法,不管是实例方法还是静态方法都可以。
Hook普通方法
被Hook的代码:
1 | package com.example.xxx; |
Hook代码:
1 | function main() |
Hook执行so函数
Hook有导出函数
通过导出函数名称找到函数地址即可进行hook:
1 | if (Java.available) { |
执行后成功hook函数返回值:
1 | // 配置好环境 |
Hook无导出函数
.so 文件被去符号,无法找到对应函数名称,通过偏移地址调用函数:
1 | function hookTest9() |
示例
1 | function main() |
1 | function main() |
脱壳
apk壳检测
1 | import zipfile |
脱壳方法
dumpDex
dumpDex-Android脱壳:https://github.com/WrBug/dumpDex
dumpDex是一个github上开源的xposed插件,可以用来脱掉当前市场上大部分的壳。
一、准备工作
首先需要root的手机一部,我使用的是华为荣耀6(android5.1),安装好xposed框架
dumpDex项目地址:https://github.com/WrBug/dumpDex
可以直接下载release的apk,也可以自行编译打包成apk安装到手机,我个人比较喜欢第二种。
安装好apk后,对于32位手机,需要将lib/armeabi-v7a/libnativeDump.so复制到/data/local/tmp/libnativeDump.so,权限设置为777。
二、开始脱壳
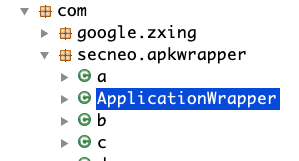
反编译apk后,根据特征发现是使用了梆梆加固
安装插件,重启手机,打开加固的apk,脱壳的后的dex会在/data/data/对应包路径/dump文件夹下
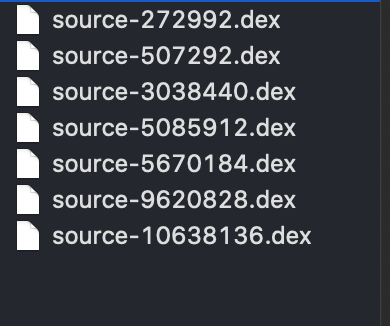
脱壳后的dex如图所示,其中有一部分是壳的dex,需要自己自行选择一下
三、补充说明
设置权限问题,GitHub上有详细说明
编译过程有可能会有让你设置签名的一个问题,直接设置成你的debug签名就可
如果加固后的包名在PackageInfo.java中没有对应的,自行加到PackageInfo.java中即可
应用有可能有卡死状况或者手机重启状况,但应该能脱出壳来,建议多脱几遍
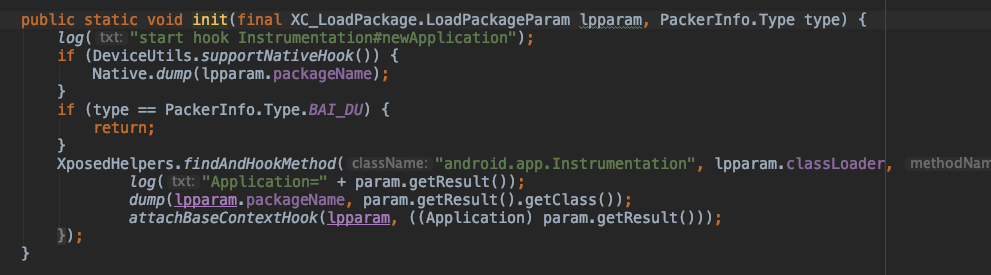
源码部分如果是百度系的壳,直接返回并有没dump,因为还没遇到过百度的壳,暂不知道具体原因
FART
1、安装镜像
从https://github.com/hanbinglengyue/FART上下载镜像,然后按照https://www.bodkin.ren/index.php/archives/513/刷机,中间没有遇到什么问题。
1
2
3
4
5
6
7
8
9adb reboot bootloader
fastboot oem unlock
fastboot flash system system.img
fastboot flash userdata userdata.img
fastboot flash boot boot.img
fastboot flash cache cache.img
fastboot flash ramdisk ramdisk.img
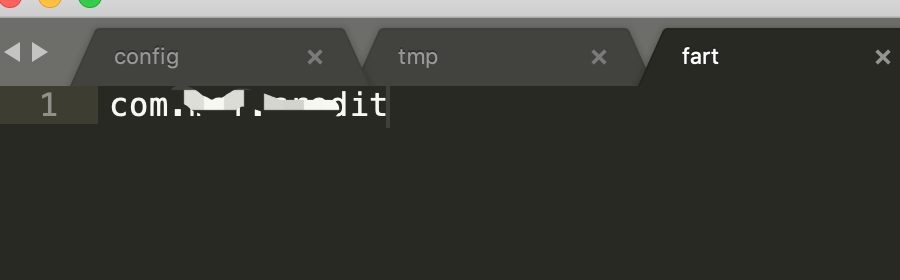
fastboot reboot2、修改fart文件并上传
将fart配置文件fart复制到/data/fart(注意文件权限问题,和换行的问题),其中,fart配置文件中为要脱壳的app包名
1
adb push ~/app_crack/fart/test/fart /data
3、查看日志确认
1
2# 在命令行输入下面的命令,然后打开app
adb logcat -s ActivityThread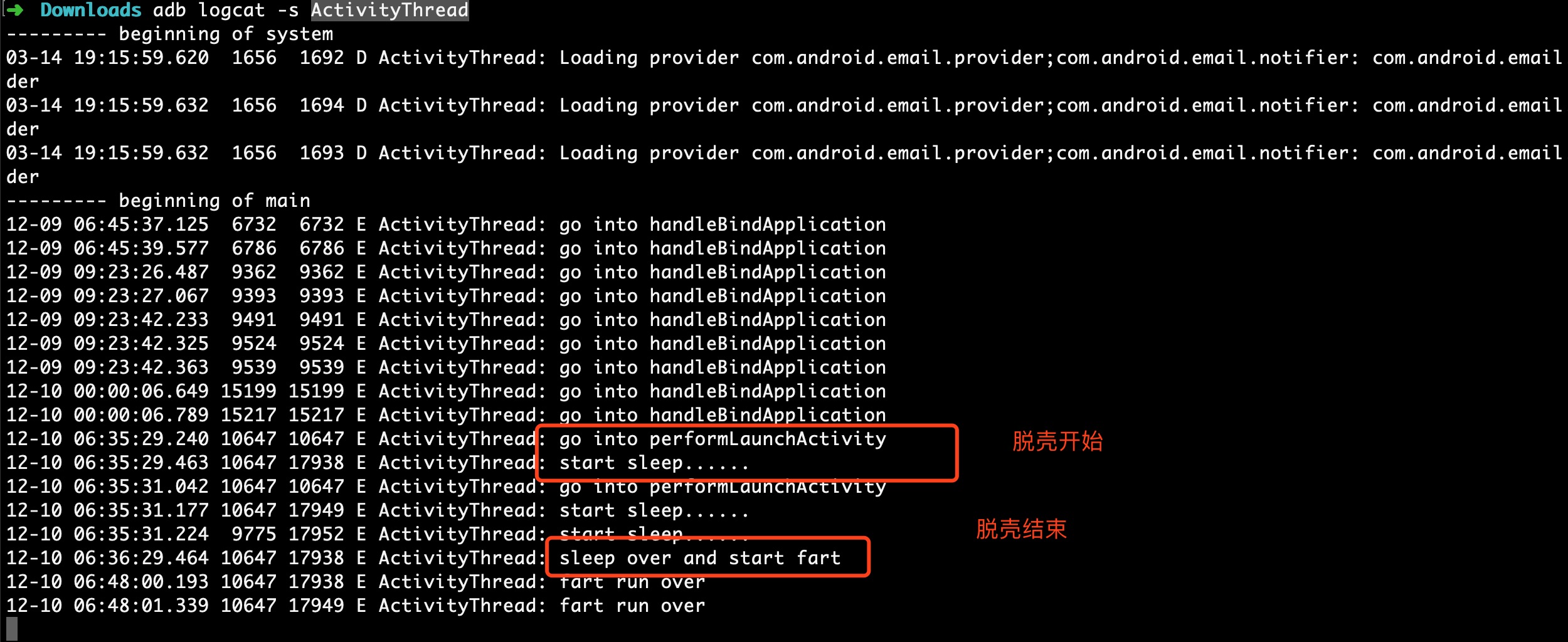
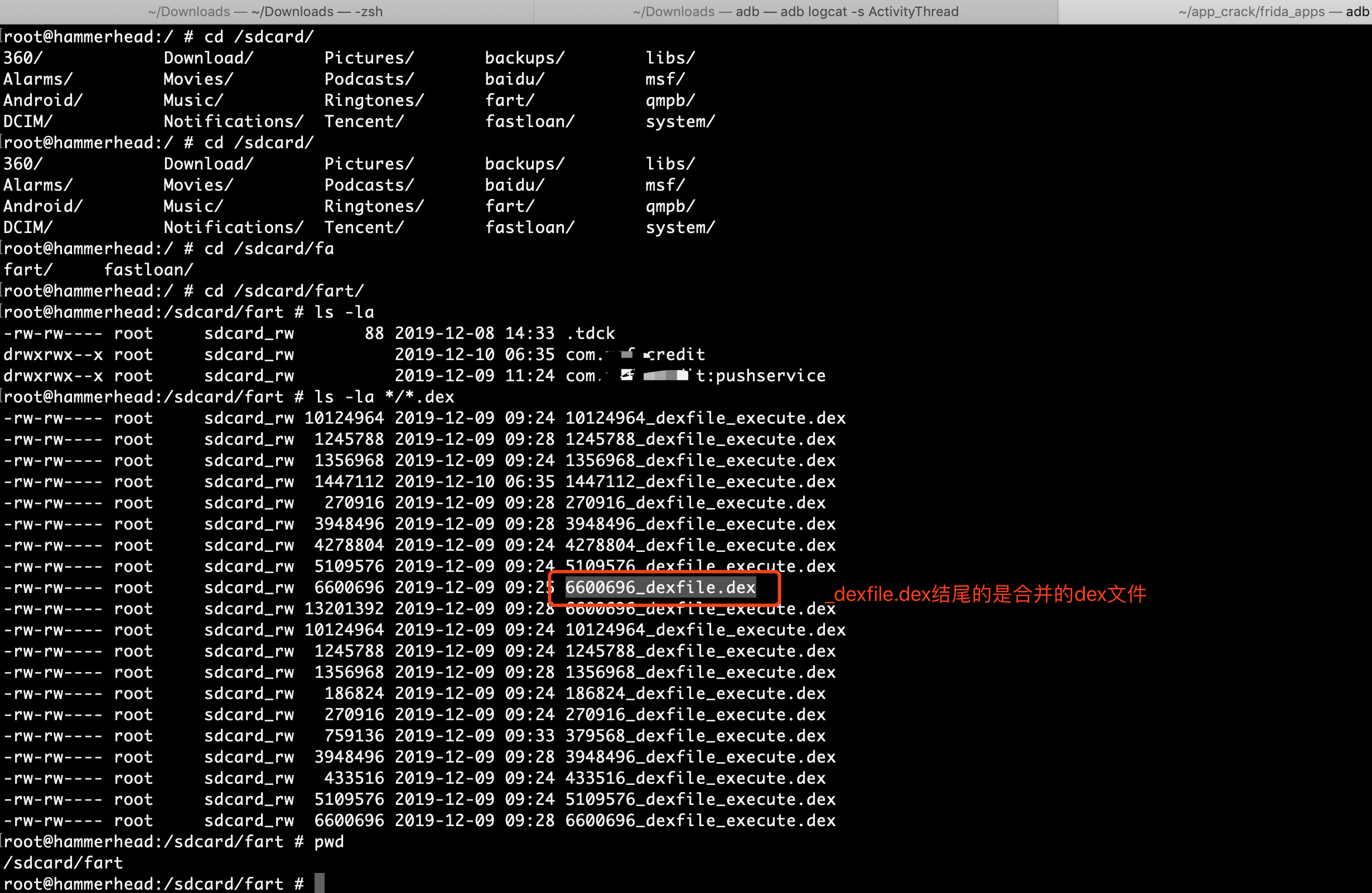
4、查看脱出来的dex
1
adb pull /sdcard/fart/包名/6600696_dexfile.dex .
Frida
https://github.com/hluwa/FRIDA-DEXDump
https://github.com/GuoQiang1993/Frida-Apk-Unpack
使用:
- 启动 APP。
- 启动 frida-server。
- python main.py。
或者可以将脚本封装成命令,就像这样:
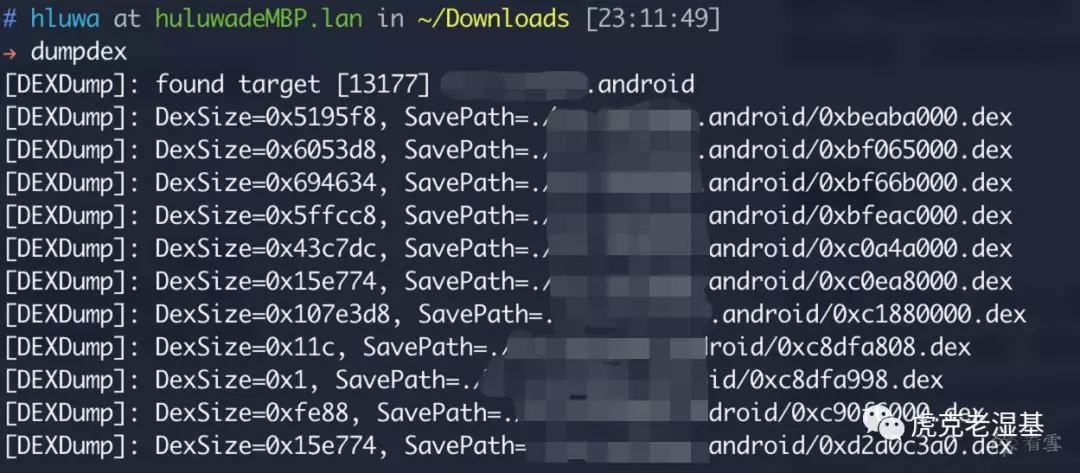
混淆
BlackObfuscator
jeb 5.1+版本反编译,运行调试java代码。
ZUC
解密:
1 | from math import ceil |

