由嘶吼主办的2020 RoarCTF线上赛,平台:https://ctf.4hou.com/。
Rank: 27
赛后无环境复现,故每题未写上flag值。
Misc
签到题
不属于Misc分类也不像签到题的签到题。
F12查看源码,发现/?url,需要GET方式传url。
尝试目录穿越及远程请求数据无效,发现file伪协议/?url=file:///etc/passwd能成功回显内容,
读index.php源码:/?url=file:///var/www/html/index.php,内容为PHP curl实现,过滤了flag关键字。
利用PHP的二次编码解析bug(bypass strpos verification)编码即可绕过过滤:
Payload:/?url=file:///fla%2567
Hi_433MHz
RF射频信号数据,以原始数据方式导入Audacity查看波形,放大,
发现摩斯密码,对照可能的flag字符串摩斯密码--..--./--.--../--....-/--..---,开头四段去掉前后的.是吻合的,手工记录所有段解密得flag。
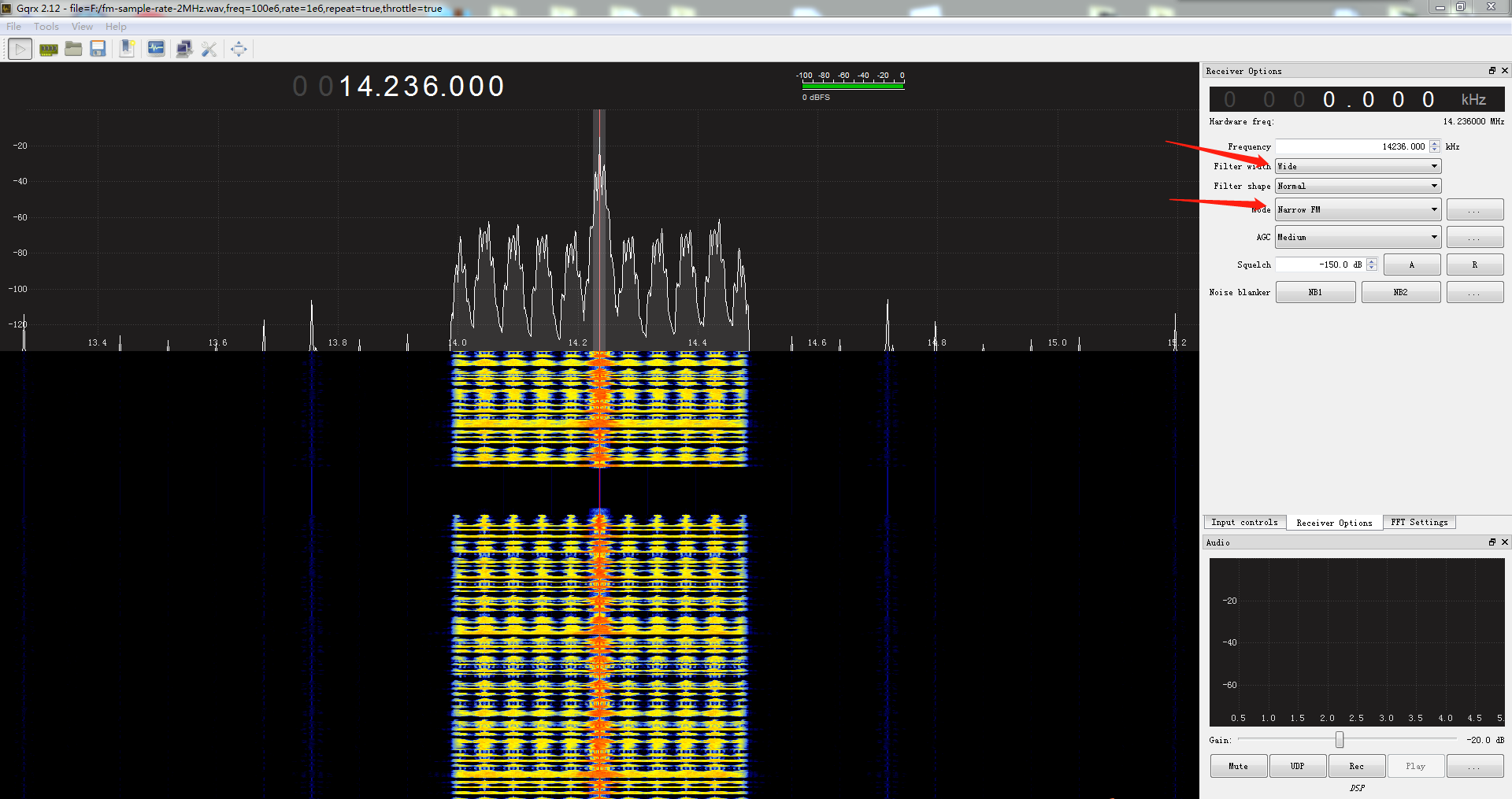
FM
FM调频信号数据,以原始数据方式导入Audacity查看波形未查出有用信息。
搜索可查看FM信号的软件,首先尝试用SDR#打开,设定好2MHz的采样率,调整频率至幅值最高处,能勉强听到人声,但噪声太大,官方原生版SDR#也未找到比较好的去噪滤波功能。
换一个软件,找到Windows平台SDR软件全家桶PothosSDR,使用里面的GQRX SDR分析,功能齐全,导入后调整 Mode=Narrow FM 及 Filter width=Wide,可以清晰听出内容,报的就是flag。
Crypto
Crypto_System
从CyBRICS 2020 - Too Secure魔改的Pedersen加密,算法描述:

已知信息 $m_1,m_2$和 $m_1$ 的 $r_1$,$m_1$ 通过因子 $r_1$ 加密得到 $c_1$,需要求出因子 $r_2$,使得 $m_2$ 通过 $r_2$ 加密得到的 $c_2$ 与 $c_1$ 相同,即产生碰撞。
对于待加密信息 $m_1$,$c_1=g^{m_1}h_1^{r_1}$,注意到 $h_1=g^{a_1}$,故 $c_1=g^{m_1+a_1r_1}$;
要碰撞信息 $m_2$ 的因子 $r_2$ 应满足 $c_2=c_1$,即 $m_1+a_1r_1 \equiv m_2+a_2r_2 \pmod {\varphi(p)}$,
又 $q$ 为 $g$ 的阶,所以有 $m_1+a_1r_1 \equiv m_2+a_2r_2 \pmod q$,
故 $r_2 \equiv (m_1+a_1r_1-m_2) \pmod q$,即可求出 $r_2$。
Exp:
1 | #python2 |
Reverse
task.py
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
from gmpy2 import *
from secret import *
assert(flag.decode().startswith('flag{')) and (flag.decode().endswith('}'))
def reverse(x):
y = 0
while x != 0:
y = y*2 + x%2
x = x // 2
return y
while True:
p = getStrongPrime(512)
q = reverse(p)
if is_prime(q):
break
n = p*q
e = 65537
m = bytes_to_long(flag)
enc = powmod(m,e,n)
#n = 158985980192501034004997692253209315116841431063210516613522548452327355222295231366801286879768949611058043390843949610463241574886852164907094966008463721486557469253652940169060186477803255769516068561042756903927308078335838348784208212701919950712557406983012026654876481867000537670622886437968839524889
#enc = 103728452309804750381455306214814700768557462686461157761076359181984554990431665209165298725569861567865645228742739676539208228770740802323555281253638825837621845841771677911598039696705908004858472132222470347720085501572979109563593281375095145984000628623881592799662103680478967594601571867412886606745
ASIS 2015 - RSASR魔改, $q$ 是 $p$ 的2进制反素数(emirp数),bin(q)=bin(p)[::-1]。
利用回溯算法按位从最高位端向中间爆破。
Exp:
1 | #python2 |
求出 $p,q$ 值,按照RSA计算方法求出 $m$ 即为flag。
1 | import gmpy2 |

